Information Gathering Using Metasploit
To attack a target we want all the informations(IP,PORTS,Version etc.) about that machine. So we need to gather these informations first. In this lesson we will discuss about that.
For Information gathering best tool is Nmap.
- Open msfconsole
- Then type Nmap
- Now you can see the all options in Nmap
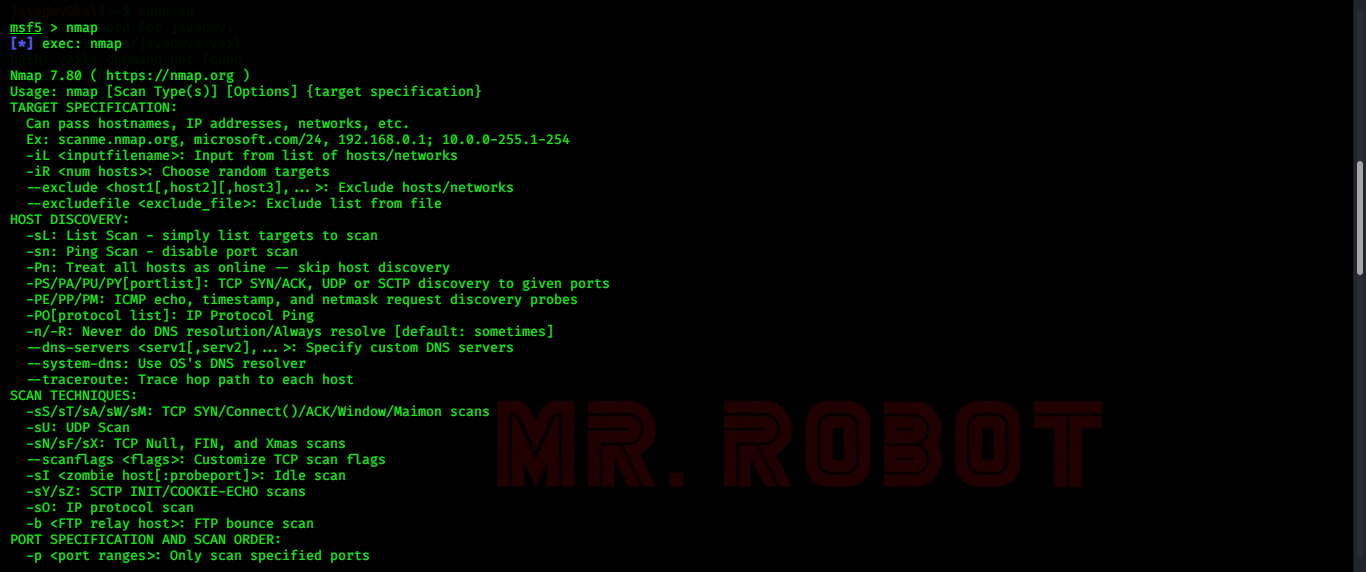


Let's check some options in Nmap. For this we are using our Metasploitable 2 machine as target.
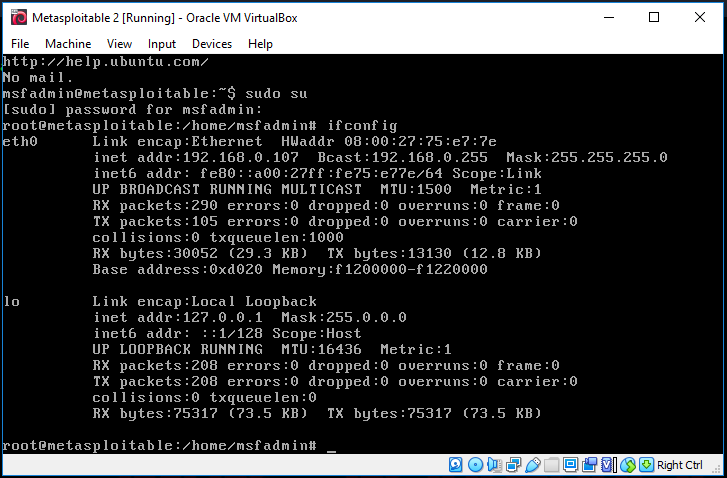
Target IP is 192.168.0.107
Now run an Nmap scan on our target.
>nmap -sT 192.168.0.1
Here 'nmap -sT' command is used for finding the open ports in the target machine.
Now we get so many open ports here.
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
23/tcp open telnet
25/tcp open smtp
53/tcp open domain
80/tcp open http
111/tcp open rpcbind
139/tcp open netbios-ssn
445/tcp open microsoft-ds
512/tcp open exec
513/tcp open login
514/tcp open shell
1099/tcp open rmiregistry
1524/tcp open ingreslock
2049/tcp open nfs
2121/tcp open ccproxy-ftp
3306/tcp open mysql
5432/tcp open postgresql
5900/tcp open vnc
6000/tcp open X11
6667/tcp open irc
8009/tcp open ajp13
8180/tcp open unknown
Using these information we use the appropriate exploit against the target.